#9 Aadhaar Card Architecture – World biggest and best biometric database
‘Aadhaar’ (aadhaar card ) is undoubtedly one of the most important Projects rolled out by Government of India. it is obviously Its world biggest biometric database.

‘Aadhaar’ (aadhaar card ) is undoubtedly one of the most important projects rolled out by the Government of India. Ambitious, one-of-a-kind, and a game-changer, ‘Aadhaar’ is on the path of delivery to every Indian resident, a ‘national identity and triggering thereby the much-desired governance system based on social inclusion, transparency & accountability. Considering India’s population of 130 crores, it is obviously the world’s biggest biometric database.
Page Contents
Aadhaar Card System Reference Architecture
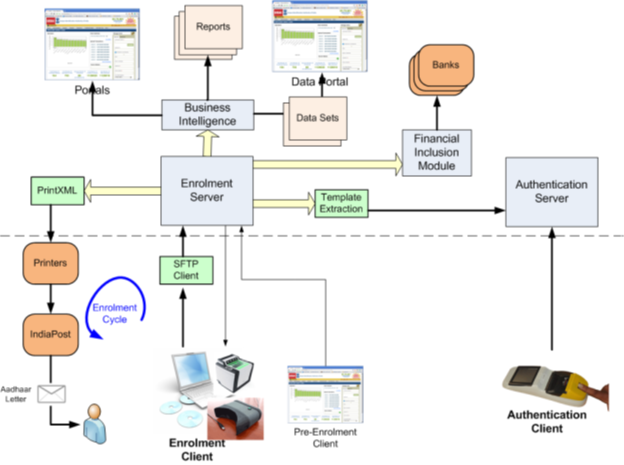
Below figure depicts the Aadhaar system at a high level.
Use of Biometrics in Aadhaar
The Aadhaar ( aadhaar card ) biometric system design has followed global best practices. UIDAI has reviewed existing state-of-the-art biometric systems, consulted with the world’s top biometric experts, conducted a proof of concept study and has built a biometric system that is currently considered to be state-of-the-art.
Multi-ABIS De-duplication System
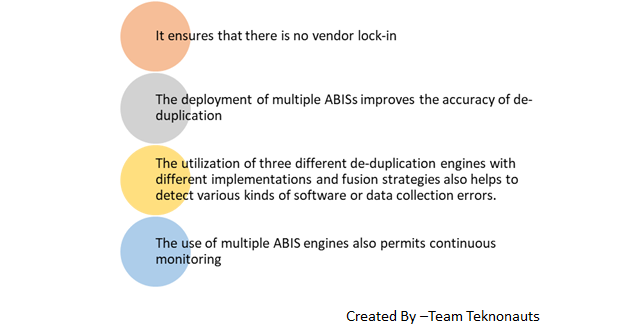
Since de-duplication at this scale (1.3 billion residents) had not been previously attempted anywhere in the world, UIDAI decided to procure 3 ABIS (Automatic Biometric Identification System) software solutions to perform biometric de-duplication as a risk mitigation strategy.
Aadhaar ( aadhaar card ) is the first ever multi-ABIS system implemented in the world, and brings significant advantages:
Biometrics in Authentication
Fingerprint and iris are the biometric modalities that are being used by UIDAI to allow residents to authenticate themselves. Online biometric authentication is a 1:1 verification of the biometric(s) presented at the time of authentication with templates generated from the data collected during enrolment or biometric updates.
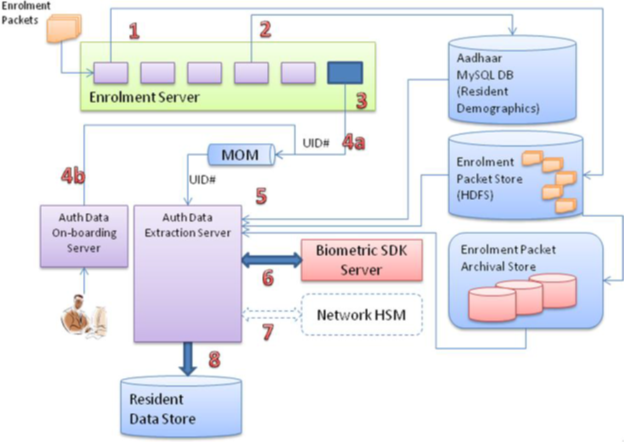
Enrolment Process Reference Architecture

Enrolment module handles entire Aadhaar lifecycle including initial enrolment, corrections, subsequent demographic/biometric updates, back-end workflow related to handling enrolment exceptions, etc. Diagram above depicts the high level picture of the entire enrolment system.
Enrolment Client
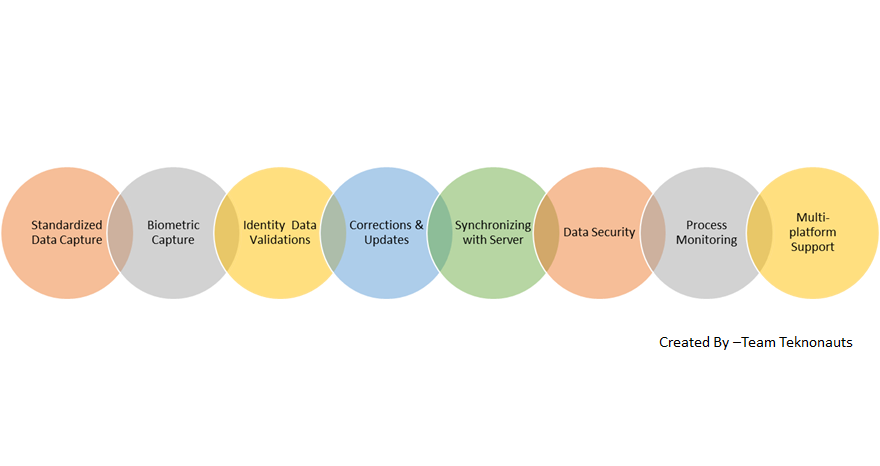
Aadhaar ( aadhaar card )enrolment strategy is based on a multi-registrar model. This means that for uniformity of data capture, process, and security, it was essential that standardized “Enrolment Client” (EC) software be created and given to all Registrars to be used by their appointed Enrolment Agencies (EAs). Enrolment client software is provided by UIDAI to use it in the field for first-time enrolment and for subsequent data updates.
key features of enrolment client-
Architecture Principles
Architecture principles used in building Aadhaar system ( aadhaar card )ensuring openness, vendor neutrality, scalability, and security. Before introducing Aadhaar architecture principles, this chapter looks at software system architecture trends over the last couple of decades and looks at some of the high impact changes in recent years. This understanding is critical in appreciating Aadhaar architecture and the reasoning behind those decisions.
Architecture Evolution & Trends
Software architecture has evolved from mainframe era to cloud computing era and as part of that change, computing, storage, and programming technologies also have evolved. Monolithic architecture has given way to large scale distributed computing architectures, proprietary storage and compute has given way to commodity computing and large scale low cost storage, user interface has changed from character based fixed green screens to highly interactive gesture based mobile interfaces, and nearly no connectivity to having pervasive connectivity. Massive increase in the amount of data managed within applications from mere in kilobytes and megabytes to petabytes and hexabytes have forced architects to rethink on design choices for computing and data store within applications.
These changes have had huge impact when building next generation, large scale applications. Subsequent sections in this chapter explore these trends, changes, and set the context for understanding Aadhaar ( aadhaar card )architecture strategy.
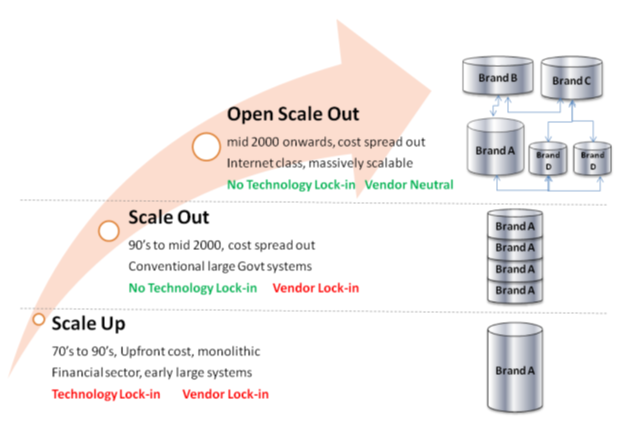
Scale-up, Scale-out, and Open Scale-out
Over the last four decades, software system architecture has evolved from a monolithic, single large server deployment to highly distributed, heterogeneous technology deployment. This has resulted in significant architecture and design shift from a vendor locked-in system to highly open and distributed system.
Scale-Up Architecture
In the 70’s and 80’s, large scale systems were designed to be monolithic and deployed in a large mainframe class machine. These systems are built using specific technologies provided by one vendor who also provide the large hardware for deploying these applications. Once you decide to build using technology provided by one mainframe (or similar large scale computing platforms) vendor, then for several years following it, application scaling, system upgrades, maintenance, etc all completely depends on that particular vendor.
Such architecture is referred to as scale-up architecture where entire system needs to scale within one machine (by adding more computing power within the machine) and that too using the technology provided by that vendor. Most of the time, significant upfront investment needs to be made planning for future growth and scaling instead of upgrading the systems at a later stage when it is really required to do so.
Scale-Out Architecture
From the 90’s, with the advent of client-server architecture, application architecture changed to support different components of an application to be deployed in different machines and allowing them to scale independently. Most of these systems were built to run on Unix or Windows environments and middleware technologies allowed components to communicate with each other across machines over a network. Large scale applications deployed within enterprises and early Internet applications followed this architecture.
Aadhaar card Application Architecture
Aadhaar application is primarily written in Java™ language using open source components and frameworks. Application is built in tune with all the architecture principles described above
Reference Client Architecture and Implementation
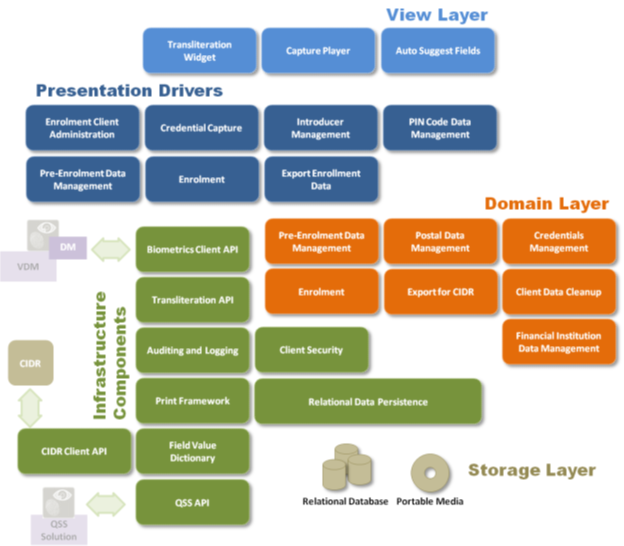
Enrolment Server Logical View
Aadhaar ( aadhaar card ) enrolment server components are highly scalable to handle million+ enrolments every day and is built to manage data stores in 1000’s of terabytes. Entire enrolment workflow is broken up into many logical stages

Enrolment Biometric Subsystem
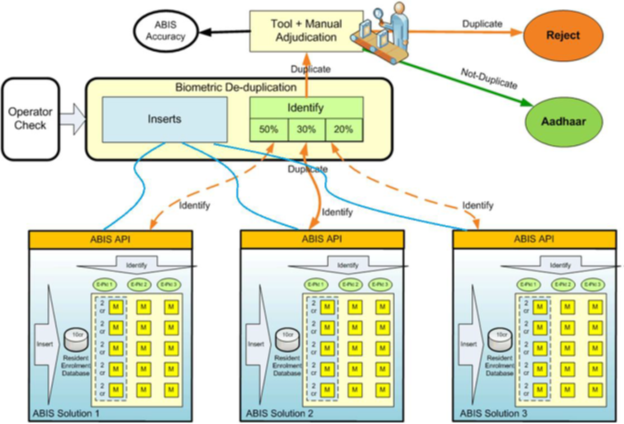
Aadhaar ( aadhaar card ) system deploys 3 independent ABIS solutions adhering to common ABIS API for multi-modal biometric de-duplication. Enrolment server needs to therefore integrate with these solutions using the ABIS API and allocate de-duplication requests as per UIDAI policy of dynamic allocation (which uses on-going accuracy and performance data to decide which solution gets maximum de-duplication requests).
Architectural requirements of multi-ABIS solution are as follows:

Following diagram depicts the multi-ABIS architecture with ABIS middleware orchestrating the insert/identify flows between 3 different ABIS solutions as per UIDAI dynamic allocation policy.
Information Privacy & Security
Application security for the above architecture cuts across all places where an un-trusted source or destination is used. The encrypted enrolment data file is uploaded in the DMZ to ensure against Trojans or malwares.
The enrolment/update data packets are encrypted by the client using public key cryptography with each data record having an HMAC which can identify any integrity violation of the data. Master keys are stored and managed within HSM (Hardware Security Module) appliance. It must be noted that the enrolment packet is constructed in memory and encrypted prior to writing of the file. All of the data, including biometrics and demographic data, is never stored in unencrypted form. The packet is encrypted with a randomly generated AES-256 symmetric session key and the key itself is encrypted with a 2048 bit public key, selected from a bank of UIDAI public keys.
Data Model Aadhaar Card
Following diagram depicts enrolment data model:
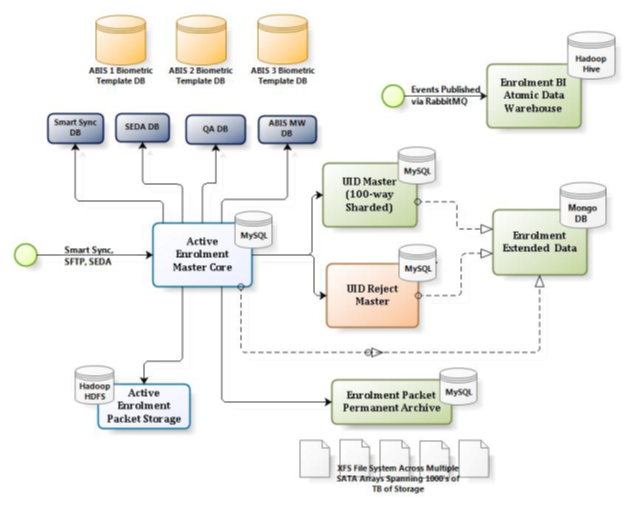
Other modules such as upload, ABIS middleware, Data Quality, Manual Adjudication, etc use an extended database of their own with link to the above core data via either EID or RefID. They can also be linked via Aadhaar number itself in the case of components that provide features at Aadhaar level. These extended databases are typically component level audits that can be archived away after a period. Analytics (BI) module is used for long term analytics/reporting where all events are stored within Hadoop Hive Atomic Data Warehouse (ADW) for long period of time. Various Hive and map-reduce jobs are run on that atomic data warehouse to derive aggregate metrics.
APIs wrap the core data models and provide uniform way to access this data via EID/RefID/UID irrespective of the state they are in (being processed, Aadhaar ( aadhaar card ) allocated, or rejected). Status tracking API, Common Search API, Advanced Search API are these core APIs. Other services such as e-KYC API, e-Aadhaar service, etc all built as wrappers on top of these core internal data access APIs.
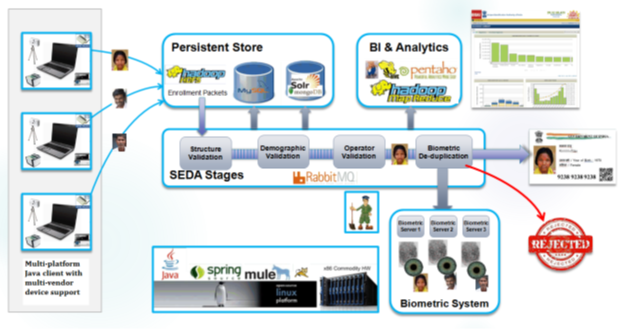
Below diagram depicts technology stack used within enrolment server module at a high level. In addition to those depicted above, there are several open source libraries used throughout the system. Following table lists the technology stack of Aadhaar ( aadhaar card ) enrolment server.
Resident Data Extraction
Enrolment server processes enrolment packets and stores the Aadhaar’s demographic data in UID Master which contains demographic and photo data. Aadhaar data that is needed for authentication has to be stored in database that offers faster read/writes and promises higher throughput. Since RDBMS and XFS based archival system cannot be used for reading resident data during authentication (100+ million reads a day) as they do not offer desired performance, it is imperative that data is extracted from enrolment data stores and stored in a high performance, distributed, read data store such as HBase.
In addition, the biometric authentication requires usage of biometric template gallery, which is biometric feature set extracted from raw biometric images. Hence, the processing of biometric images also has to be performed as part of preparing data for authentication purposes.
Technology Platform
Application modules are built on common technology platform that contains frameworks for persistence, security, messaging, etc. The Platform standardizes on a technology stack based on open standards and using open source where prudent. A list of extensively used open source technology stacks is given below:
Spring Framework – application container for all components and runtime

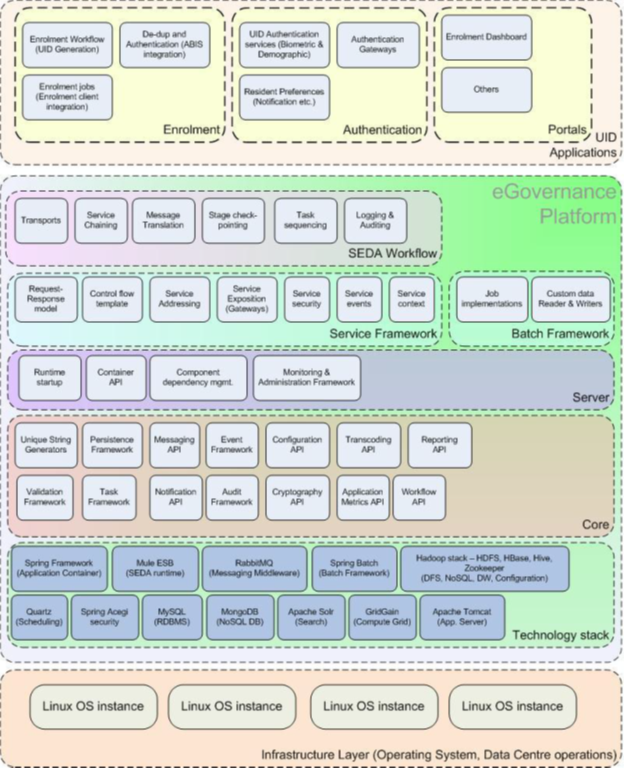
The diagram below depicts the e-Governance platform as a set of layered technology building blocks that are used to build applications.
Conclusion – ( aadhaar card )
Aadhaar ( aadhaar card ) system is built purely as an identity platform that other applications, Government and private, can take advantage of. A sound strategy and a strong technology backbone enabled the program to be launched ahead of plan in Sept 2010 and reach the kind of scale that was never achieved in any biometric identity systems across the world. In less than 4 years since launch, Aadhaar system has grown in capability and more than 600 million Aadhaar numbers have been issued so far using the system.
Entire technology architecture behind Aadhaar is based on principles of openness, linear scalability, strong security, and most importantly vendor neutrality. Aadhaar software currently runs across two of the data centres within India managed by UIDAI and handles 1 million enrolments a day and at the peak doing about 600 trillion biometric matches a day to meet its peek needs. In coming years Aadhaar system will cover rest of the country proving identity to more than 1.2 billion residents in India and its electronic usage (Authentication, e-KYC, etc) is expected to grow exponentially.
Knowing Architecting of Aadhaar system keeping the scale, security, ecosystem design, and most importantly the constraints of an e-Governance system, is a lifelong learning experience.
Explore more at Teknonauts
Reference Link
Aadhaar card conceptualization
Aadhaar card conceptualization
Disclaimer
Architectural concepts and components explained in this article are taken from public information (provided in reference link). We have provided our own explanation for knowledge purposes only.

Awadhesh Pratap Dwivedi is an IT industry leader with over 13+ years of experience. He is excellent at providing an easy solution to complex business problems with his tremendous problem-solving skills. Currently, he is working with Oracle as a Principal Solution Engineer.







